Identity theft occurs when your personal information is stolen or used without your permission, possibly with the intention to defraud you or others.
Here are some of the various identity theft tactics which an internet user might encounter as they surf the web. Becoming aware of these threats, avoiding and reporting them are the most effective means of protecting your account information from identity thieves.
Phishing
Phishing is a scheme that utilizes legitimate looking emails, pop-up messages, and phony websites to deceive users into revealing their personal or account access information. "Phishers" collect information, such as name, address, date of birth, and social security numbers, which they use to open new accounts under your name or access your existing accounts.
Detecting Phishing
Phishing emails, websites, and messages are all designed to deceive and often look similar or identical to emails or websites of legitimate businesses. A common phishing tactic is to send out an email or message that creates a sense of urgency by, for example, falsely notifying you of the closure of an account, of the need to verify your account information, or of the possibility that your account has suffered a security breach. Such communications will often carry the logo and name and have the look and feel of a legitimate firm´s communications.
Protecting Yourself from Phishing
-
Use Security Software - many companies offer security software with anti-phishing features. Such programs will assist you in filtering junk emails and identifying possible phishing threats.
-
Never communicate personal information through email or pop ups
-
Beware of call to action emails such as "You account will be terminated if you do not update your information."
-
Be careful when typing web site addresses; misspelling a URL might lead you to a phishing web site.
-
Use spam detectors to block malicious or fraudulent emails.
-
Keep your Windows operating system and security software updated to ensure you are armed against the latest threats.
-
Use the most current version of your internet web browser, which will contain the latest security features.
If you receive a suspicious email or message, contact the company being misrepresented via a secure channel. If you ever receive an email or message which you believe misrepresents SogoTrade, please email
[email protected]
or call SogoTrade support 646-885-6486. Please remember: SogoTrade will never solicit account information via email or popup.
Pharming
Pharming is a more advanced form of Phishing. In this scheme, unsuspecting people are directed to a malicious web site that is similar or identical in look and feel to a legitimate website. Once on this site, thieves will attempt to collect your personal information, login names, and passwords.
Protecting Yourself from Pharming
-
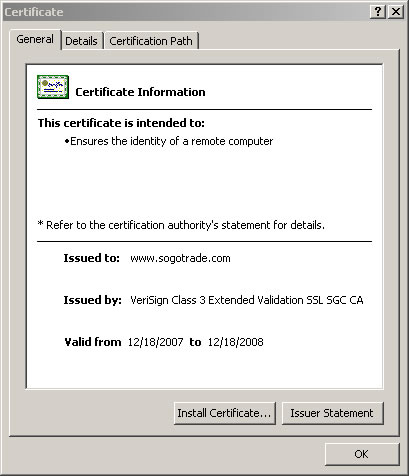
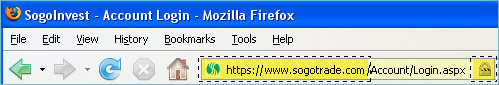
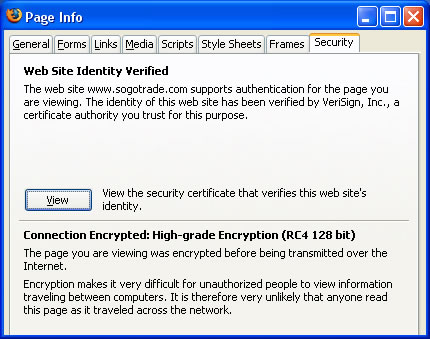
When you visit a web site to log on to your account or complete a purchase, please ensure that the site offers SSL protection. SSL stands for Secure Socket Layer and is a communication protocol used to secure data transfers over the internet by mathematically transforming a message so its contents are concealed to everyone but the intended recipient. SogoTrade uses industry-leading 128-bit VeriSign SSL encryption technology throughout its website to ensure that your personal data is at all times protected from eavesdropping, tampering, and forgery.
-
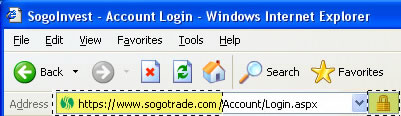
The authentic SogoTrade website will display a clickable VeriSign Certificate Icon located at the bottom of each page.
Once clicked, you will be able to view the SSL certificate for www.sogotrade.com which identifies Wang Investments as a valid business that encrypts all sensitive information entered on the SogoTrade website before it is transmitted.
Internet Explorer 6.0
Internet Explorer 7.0
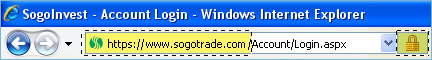
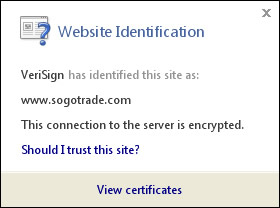
Firefox 2.0
-
Indicators of authenticity can spoofed by hackers, therefore, these checks are not absolute indications of a websites safety. It is always important to check your account statements, account information, and account history frequently to ensure that no unauthorized transactions have taken place.
As with Phishing emails and messages, if you believe that a company´s web site is being misrepresented, contact that company directly through a secure and trusted channel. If you ever visit a website that you believe misrepresents SogoTrade, please email
[email protected]
or call SogoTrade support 1-646-885-6594.
Trojan Horses
A Trojan horse is a program that installs malicious code onto your computer. Trojan horses are often hidden and harmless until an action is executed such as clicking on a link in an email. Once the code is activated, a hacker may be able to capture your keystrokes and collect your userID, password, and other sensitive information. Trojan horses will often be included in viruses, spyware, and worms or embedded in various "
free
" downloads such as screensavers.
Protecting Yourself from Trojan Horses
-
Use Security Software - many companies offer security software with features that provide inbound and outbound firewall protection. These help block Trojans, spyware, and key loggers.
-
Keep your operating system updated. An updated operating system behind a firewall is the best defense against Trojan and spyware installation.
-
Use the latest version of your internet browser which will contain the latest security features.
-
Only open attachments from trusted sources.
-
Use caution when engaging in peer-to-peer file sharing. Trojans can sit within file sharing programs waiting to be downloaded.
Spyware
Spyware is malicious software installed on your computer without your permission and is designed to collect information about you. This information can range from your web surfing history to your login names and passwords.
Protecting Yourself from Spyware
-
Use security software - many companies offer security software that will detect and remove spyware from your computer and block new spyware from being installed.
-
Keep your operating system updated. An updated operating system behind a firewall is the best defense against Trojan and spyware installation.
-
Use the latest version of your internet browser so you have the latest internet security technology which may be able to filter sites that install Trojans.
-
Read privacy policies carefully before installing any software. If you have any suspicions, don´t install the software.
-
Try to avoid suspicious websites that might install spyware on your computer.